Last year we released
a stand-alone security tool to check if your DNN site is configured correctly
from security point of view. This tool was very well received by our customers
and community. In light of the recent security incident on DNN sites, we
decided to update this tool to detect additional misconfigurations.
Let’s take a look.
New Audit Checks
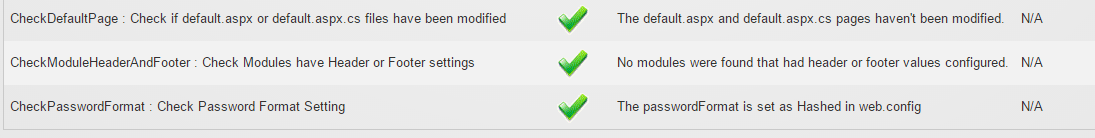
Six new checks were added under Audit Checks tab – “Check
Default Page”, “Check Module Header and Footer”, “Check Password Format”,
“Check Disk Access”, “Check SQL Risk”, and “Check Allowable File Extension”.
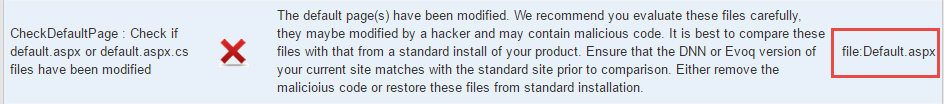
Check Integrity of Default Page
During the recent security incident, we noticed that the
hacker had tweaked the default.aspx or default.aspx.cs files to add hidden
links or iframes. We have added checks to compare these two files from your
current site with that from a standard installation of the version you are
using.
Once this tool flags an error by showing ‘X’ next to the
check, you are advised to compare both of these files using a file-diff utility
with the standard versions to see if the changes were genuine. Remove the
malicious script tags from the files or best revert back to originals.
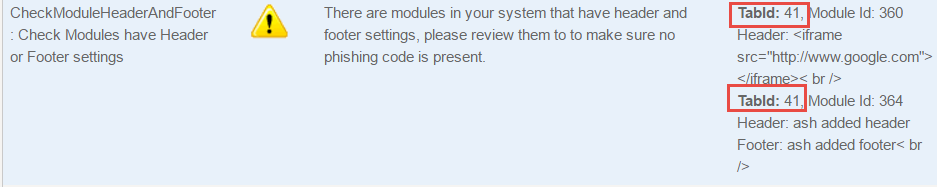
Check Module Header and Footer
During the recent security incidence, we noticed that the
hacker was taking advantage of module’s header and footer settings to generate
malicious Html. This check lists all the modules that contain Header or Footer
settings. Please note that not all settings are malicious in nature. Tool lists
all the modules containing headers or footers, their Tab Ids and Module Ids are
listed. Look for suspicious settings such as iFrame.
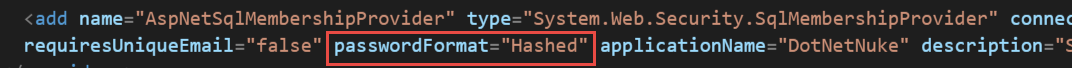
Check Password Format
It is recommended that sites use “Hashed” password format.
This setting prevents anyone (even genuine SuperUsers) from getting back to the
password in text format. If the setting is “Clear” or “Encrypted”, change it to
“Hashed” in the web.config. Note, this change will not change the format of
existing accounts, only new passwords will be hashed.
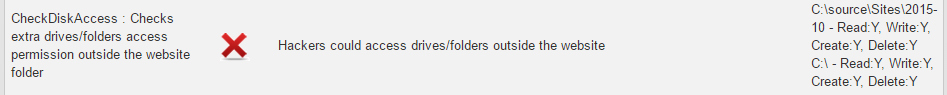
Check Disk Access
Often the user running App Pool has more permission than it
needs. The purpose of this check is to indicate if this user has permissions
outside of the DNN website folder.
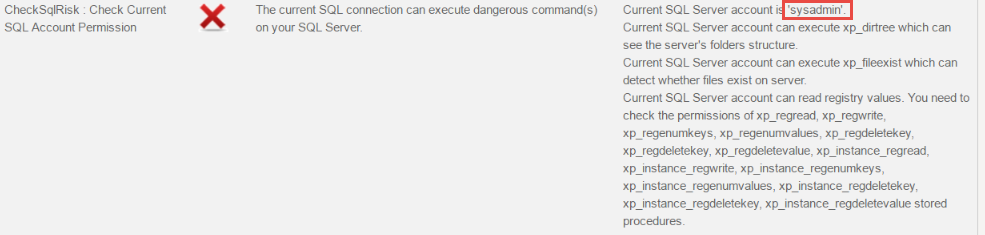
Check SQL Risk
Often times the SQL Server user used to access
database from DNN may have more permission than it needs. It’s good to ensure
at least user doesn’t have “sysadmin” permission.
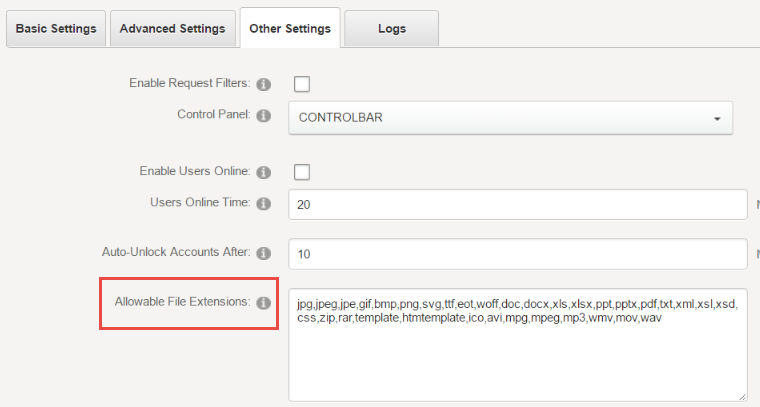
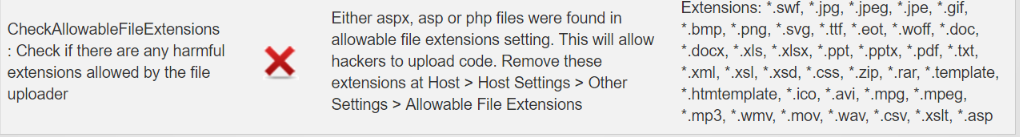
Check Allowable File Extension
DNN has very strict file extension rules, that it does
not allow users to upload files that can execute code – files such .aspx, .asp
or .php. In fact, DNN allows uploading of files whose extensions are defined
under Host > Host Settings > Other Settings > Allowable File
Extensions. However, at times SuperUser may add an extension temporarily, but
fail to remove it. The purpose of this check is to identify such
misconfiguration.
New Tabs
There are two new tabs added - "Recently Modified Files" and "Recently Modified Settings"
Recently Modified File
This tab shows the last 50 files modified within the DNN
website folder. Tab consists of two sections - the top one showing "High Risk" files and the bottom one "Low Risk".
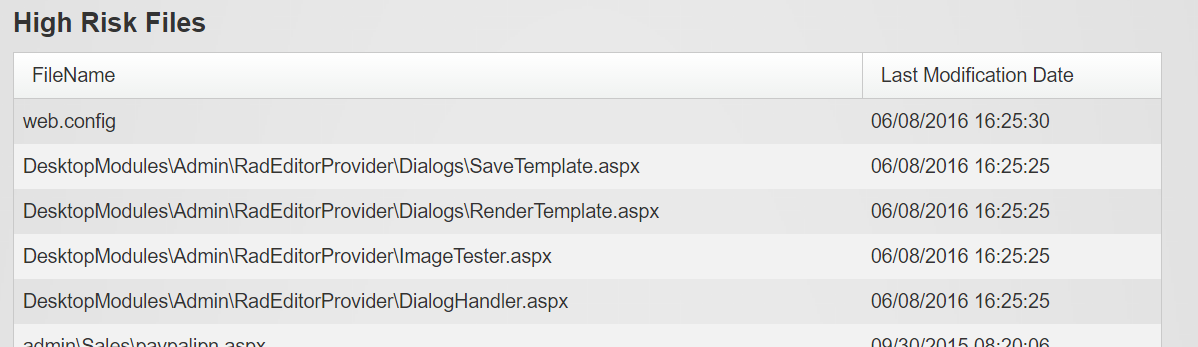
High Risk Files
The high risk files are those that have extension of .aspx, .asp and .php. They are deemed high-risk as they can execute code. It is important to note that DNN and Evoq ships several .aspx files in the default installation. Moreover, some of the other modules may also deploy .aspx files. What you really need to look at is the time stamp of such files and try to think if you have had done any system changes when these files were modified. System changes include activities such as DNN / Evoq upgrade, brand new install, module install / uninstall / etc.
In addition to .aspx, .asp and .php file extensions the high risk area also lists default.aspx, default.aspx.cs and web.config file.
Again, one need not panic seeing files listed here. What one needs to do is look at the last modified date and correlate that to any system activity that you have performed.
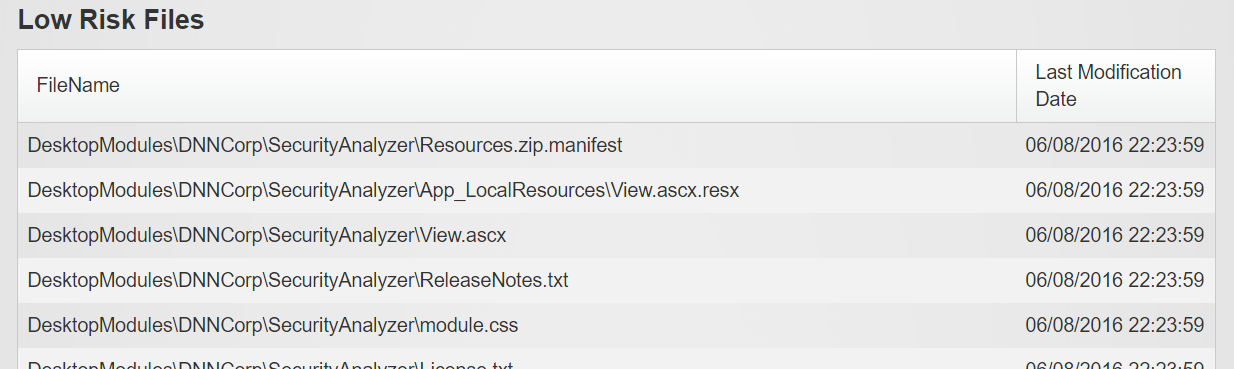
Low Risk Files
This section lists all files from your website folder except the ones listed above. You may see cache files, images, etc.
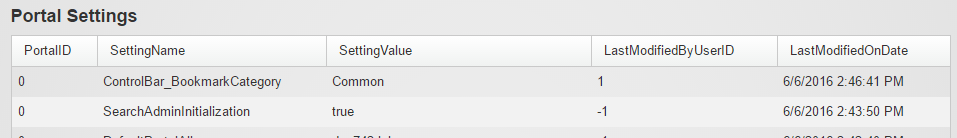
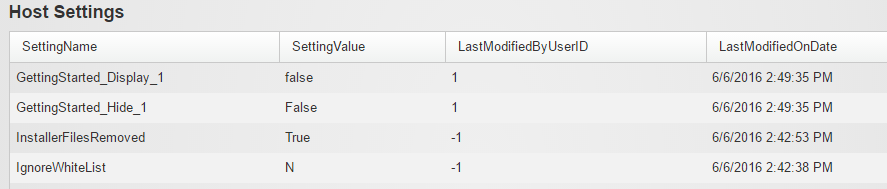
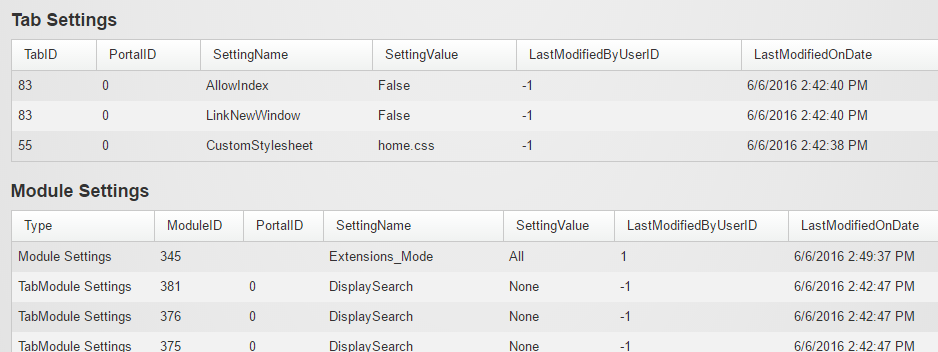
Recently Modified System Settings
One of the symptoms of the recent hack was that a number of
Host Settings got updated, including the SMTP setting. This tab lists the 20 most
recently changed settings in the following categories – “Portal Settings”,
“Host Settings”, “Tab Settings” and “Module Settings”.
Again, look for suspicious activities here.
Portal Settings
Host Settings
Tab and Module Settings
Auto Deletion of Certain Install Files
Tool deletes the following files from Website Root\Install
folder as soon it gets install:
·
DotNetNuke.install.config
·
DotNetNuke.install.config.resources
·
InstallWizard.aspx
·
InstallWizard.aspx.cs
·
InstallWizard.aspx.designer.cs
·
UpgradeWizard.aspx
·
UpgradeWizard.aspx.cs
·
UpgradeWizard.aspx.designer.cs
·
Install.aspx
·
Install.aspx.cs
·
Install.aspx.designer.cs
These files are no longer needed once installation is
completed. We realize that some DNN users want to continue to use Install.aspx
and Install.aspx.cs after installation. They may replace them on their own and
their own risk. The recent exploit was in InstallWizard.aspx file and that must
be removed.
In any case, most of these files are placed back with the upgrade
package, and removed again after upgrade is done.
Tool’s Version
The first version of this tool was released as 1.0.0. The
same version shipped with DNN version 7.4.1. During DNN 7.4.2, we incremented
the tool’s version to 1.0.1. Further to that, we incremented the tool’s version
to 8.0.0 during DNN Platform 8.0.0 (Evoq 8.3.0) release. The version number was
incremented to keep in synch with DNN Version, as such there wasn’t a major
change in the tool. Later, tool’s version number was incremented to 8.0.1
during DNN 8.0.1 release.
As of this writing, the latest version of this tool is
8.0.2.
Backwards Compatibility
Security Analyzer can be installed on DNN versions 6.2 and
above. This tool has more features than the version being shipped with the
latest shipping DNN or Evoq products. Please note that the last shipping
releases are DNN Platform 8.0.3 and Evoq 8.4.2 at the time writing.
Source Code
Security Analyzer is open source as well; the source code
can be found here: https://github.com/DNNCommunity/SecurityAnalyzer
Reporting New Issues
Please enter new issues here on Github: https://github.com/DNNCommunity/SecurityAnalyzer/issues
How to Install
This tool is shipped as a standard DNN Module. Simply
install it using Host > Extensions. Once tool is installed, it is available
on the page Host > Security Analyzer
Acknowledgements
Besides Engineers from DNN Corp, we want to thank community
members Brian Dukes and Timo Breumelhof for testing the tool and providing valuable
feedback. Additionally, Mitchel Sellers, Will Strohl and Richard Howells have also provided suggestions..
Download
Install package can be downloaded from here: https://github.com/DNNCommunity/SecurityAnalyzer/releases
Ensure to download the version with “Latest Release” tag.
Additional Questions
Some of the above discussions are very technical in nature,
and may not be easy to understand. Ask questions in DNN Forums or as comment here for
clarification. If you are an Evoq customer, please feel free to open a ticket
with Support team.